Brian Smith
Brian Smith
bsmith@enernex.com
865-770-4853
Access to data from the wide range of Intelligent Electronic Devices (IED) and sensors, also referred to as field devices, deployed throughout the transmission and distribution field environments is often at the forefront of current discussions within most utilities. A key driver for this focus is that data available from field devices has become valuable for many business purposes beyond that of the traditional power systems operations footprint. Technology evolution of field device communications interfaces and the wide variety of communication solutions available to utilities have made the use of a multitude of field device data a realistic and attainable goal.
One significant challenge for utilities is the hidden complexity that arises when exploring options to provide business access to data available within field devices while at the same time addressing the need to ensure the security of the field devices themselves. Both data accuracy and integrity are critical for business and operational decision-making. A further complicating factor is that field devices range from single function low-end devices to complex multi-function devices that support critical power system protection, automation, or control applications. In most cases, T&D field devices are not as robust as their traditional IT counterparts when it comes to processor and communications capacity and issues such as resource consumption are a significant worry when additional communications interfaces beyond the primary application are considered.
Some utilities are already amid this challenge as they start to examine existing system deployments. Many of these systems were deployed with a purpose-built philosophy where the field device, communications, and data collection were all coupled with and dedicated to a single function or application. Other systems have evolved from pilot projects that were focused on validating fundamental application concepts and not focused on data integration and security considerations.
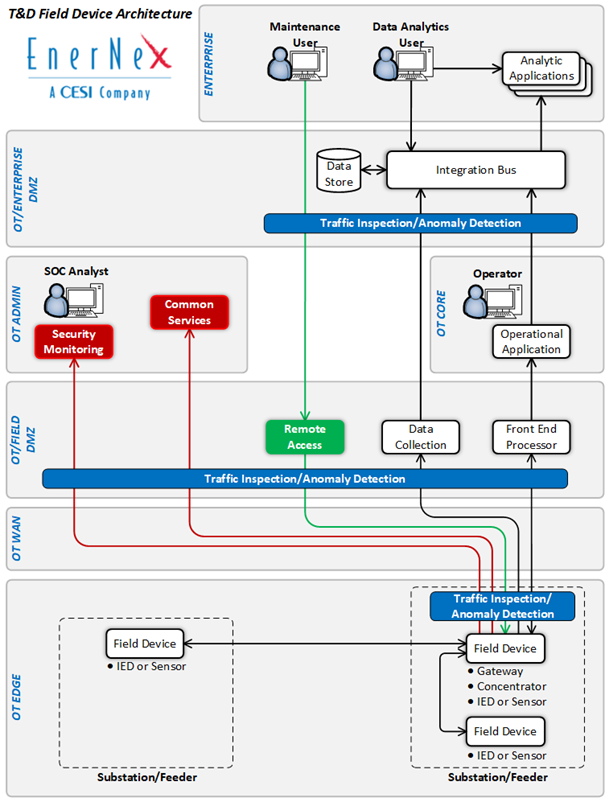
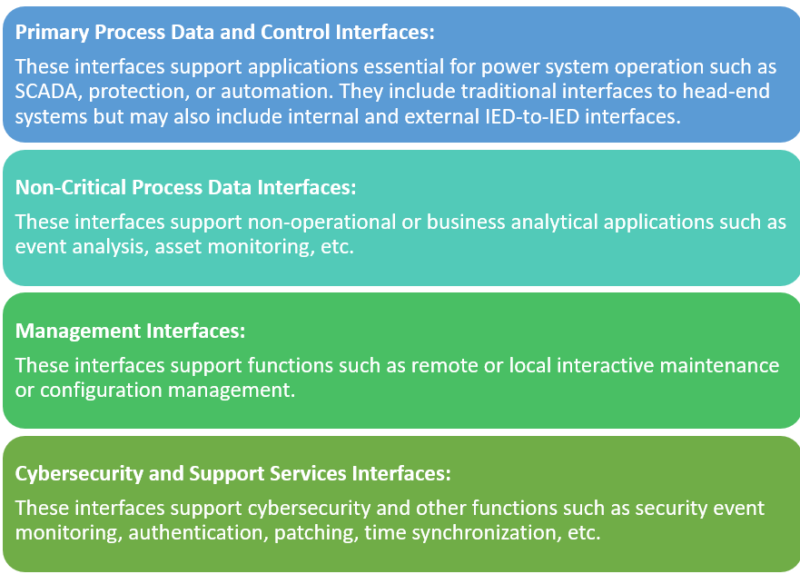
To address field device cybersecurity challenges, utilities must have an architecture reference model and roadmap to get to the desired future state. Two elements that are critical in supporting the utility’s agility in responding to evolving business and cybersecurity needs. A key first step in creating a reference architecture is to develop a holistic view of all potential interactions, both current and future, that may occur with any T&D field device. Only then, will certain interdependencies start to emerge that were difficult to identify from what had previously been disjointed snapshots of specific interactions with the field devices. While it is unlikely that any single device supports all identified interfaces, the superset of data flows provides a path to develop a reference architecture that addresses both data integration and security. One way to organize this view is to focus on four categories of logical interfaces on a T&D field device:
Once this high-level view is created, it becomes easier to begin the process of creating a T&D field device architecture that addresses operational, business, and cybersecurity needs. Key aspects of this second architecture step should include:
- Minimizing Direct User Access to T&D Field Devices – A key cybersecurity objective is to minimize the number of people that have direct access to any T&D field device. Users that only need access to the data within the device should have access to data via secondary repository and not granted direct access to the device.
- Minimizing Non-Critical Machine-to-Machine Process Data Interfaces to T&D Field Devices – In many cases, data available within T&D field devices is valuable to more than a single utility application. The architecture should support decoupling of the data acquisition function from the analysis and processing functions of the applications utilizing a utility integration bus or similar solution. Using this model, a single data acquisition element can potentially support multiple non-critical applications. It is important to note that data decoupling must not include critical applications essential for power system reliability as the additional components between the end device and application may negatively impact these applications.
- Prohibiting Direct User Access to T&D Field Devices from Outside the OT Environment – Access granted for users that are allowed to remotely connect to a field device for maintenance and management functions should be strictly managed. Although only required for assets defined as Medium Impact Bulk Electric System Cyber Systems, the NERC model of an intermediate system implemented to manage remote field device access is an effective model to implement for all field device remote access. Key elements of this include role-based access control, least privilege, multi-factor authentication, and encryption.
- Monitoring and Configuration Management of T&D Field Devices – While this has traditionally been a manual process in the past, utilities should implement active/online field device monitoring and configuration management solutions.
- Creation of Network Segmentation and Security Zones – A fundamental cybersecurity goal is to contain a security breach to the smallest area possible and flat networks that span multiple locations or functions will not accomplish this. Logical segregation by location and more granularly by function are essential to the resilience of the system and critical functions. The architecture should include traffic control and monitoring at the boundary points of the logical security zones. Additional anomaly detection solutions deployed around head-end systems as well as field devices supporting critical functions such as power system protection or automation should also be considered.
- Pushing Data from the OT Environment to the Enterprise – Another cybersecurity goal is to minimize the logical ingress from a lower trust environment (enterprise) to a higher trust environment (OT) by utilizing mechanisms to push data.
Once developed, a T&D Field Device Architecture should be seen as a starting point rather than the destination. As with any architecture effort, governance is just as essential to the success of the effort as is technology.
Want to know more about how EnerNex can support your T&D Field Device Architecture efforts? Feel free to contact me at bsmith@enernex.com to discuss. EnerNex is uniquely qualified to assist you as our staff has decades of experience in cyber security, utility automation, IT, OT, and communications systems from both vendor and utility perspectives.